Security cam blog posts on Tumblr
Room with a View

When the Perlmeister is on the road, he likes to know what's going on at home. Armed with just two scripts, he draws on the Tumblr API to store snapshots cyclically from his home security camera.
When I'm traveling, knowing that my home is threatened neither by fire nor by an invading band of thieves contributes greatly to my sense of well-being. To avoid phoning my neighbors to satisfy my security cravings, I installed a panning camera to keep a watchful eye on the skyline of San Francisco through my living room window (Figure 1). The Foscam FI 8910W [1], which costs about US$ 60 and includes a WiFi connection, supports remote control via the Internet and lets me stream the video to my mobile phone – no matter where I happen to be.

Quirky Camera
Before you indulge in impulse purchases, be warned: The cheap Foscam camera has some annoying quirks. For example, when it's dark, the camera always turns its infrared LED ring on after rebooting, which happens every now and then for some unknown reason. This feature sounds useful at first, but if the camera is set up directly in front of a reflecting window, the whole thing turns into a fiasco, with the camera dazzling itself until someone notices and switches off the infrared ring by hand.
Thus far, customers have waited in vain for a firmware update that rescues them from this feature. "You get what you pay for," as people say laconically here in the US. Also, the camera's web interface looks like a relic from the last century: Users are given a jerky video stream and can use the control buttons at the top left to pan the camera head about 300 degrees laterally and tilt 120 degrees upward (Figure 2).
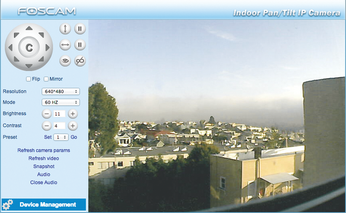
The fact that the built-in Foscam server wants you to supply your password in plain text via HTTP instead of via HTTPS is another faux pas that rational users will tend to counteract with a VPN if they need to transmit images over the Internet.
If your camera is set up at home and you want to access it from the outside, your router's firewall will need to use port forwarding to forward the incoming requests. Because the camera works with a dynamic DNS service, the web interface is always accessible at the same URL, such as http://<XXX>.myfoscam.org:5148, independent of the dynamically assigned WAN IP.
On My Mark – Blog!
Because I happen to own the camera, I have to try to make the best of it. One of my first conclusions is that it makes more sense to grab snapshots regularly with the camera and dump them onto the Internet, instead of dialing up the camera periodically to make sure everything is okay. A script can then line up the still images on a web page – and one look is all it takes for a daily routine check. So, that is exactly my plan for this month's Perl column.
To help me in this noble cause, I noticed that the Tumblr microblogging platform, which my employer, Yahoo, acquired about six months ago, has a programmable API [2]. A quick check on CPAN showed that avid open source programmers had already published a matching Perl module named WWW::Tumblr. The rest was clear sailing: A cron job executes the script presented in Listing 2 several times a day and grabs a snapshot with the camera.
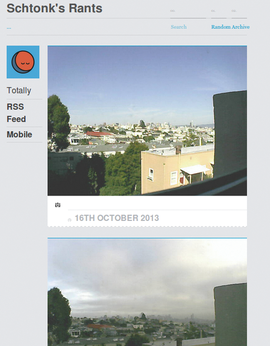
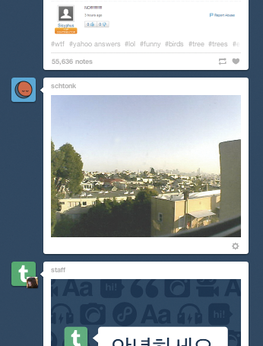
The script then routes the image via the API to my Tumblr blog, which shows the messages in reverse chronological order and offers all kinds of social platform bells and whistles such as Like buttons or reblog functions (Figure 3). Because most Tumblr users follow several blogs, you can add the sequence of home security images to your follow list and consume them along with other postings (Figure 4).
OAuth Grants Access to Tumblr Blog
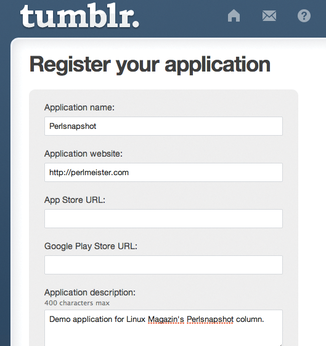
For the tumblr-post Perl script to be allowed write access to a user's blog automatically, you need to register it as a Tumblr application. Additionally, the user needs to grant the application appropriate rights. These steps are described in Tumblr's API documentation [2].
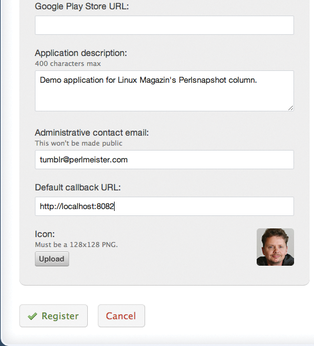
Figure 5 shows the registration process for the Perlsnapshot test application, and because it is a script – and not an app for the iPhone or an Android device – I have left the App Store URL and Google Play URL fields blank.
The Default callback URL, that is, the Web address that Tumblr invokes with the generated access tokens after authorization by the user is http://localhost:8082 (Figure 6). As an application icon, I just uploaded a 128x128 pixel self-portrait.
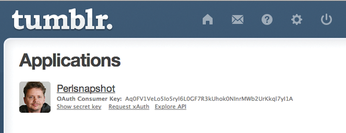
After clicking on Register below the completed form, Tumblr shows you a consumer key and a secret key (Figure 7). These two hex strings identify a registered Tumblr application, which in turn is allowed to ask users for access rights.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
Systemd Fixes Bug While Facing New Challenger in GNU Shepherd
The systemd developers have fixed a really nasty bug amid the release of the new GNU Shepherd init system.
-
AlmaLinux 10.0 Beta Released
The AlmaLinux OS Foundation has announced the availability of AlmaLinux 10.0 Beta ("Purple Lion") for all supported devices with significant changes.
-
Gnome 47.2 Now Available
Gnome 47.2 is now available for general use but don't expect much in the way of newness, as this is all about improvements and bug fixes.
-
Latest Cinnamon Desktop Releases with a Bold New Look
Just in time for the holidays, the developer of the Cinnamon desktop has shipped a new release to help spice up your eggnog with new features and a new look.
-
Armbian 24.11 Released with Expanded Hardware Support
If you've been waiting for Armbian to support OrangePi 5 Max and Radxa ROCK 5B+, the wait is over.
-
SUSE Renames Several Products for Better Name Recognition
SUSE has been a very powerful player in the European market, but it knows it must branch out to gain serious traction. Will a name change do the trick?
-
ESET Discovers New Linux Malware
WolfsBane is an all-in-one malware that has hit the Linux operating system and includes a dropper, a launcher, and a backdoor.
-
New Linux Kernel Patch Allows Forcing a CPU Mitigation
Even when CPU mitigations can consume precious CPU cycles, it might not be a bad idea to allow users to enable them, even if your machine isn't vulnerable.
-
Red Hat Enterprise Linux 9.5 Released
Notify your friends, loved ones, and colleagues that the latest version of RHEL is available with plenty of enhancements.
-
Linux Sees Massive Performance Increase from a Single Line of Code
With one line of code, Intel was able to increase the performance of the Linux kernel by 4,000 percent.

