Monitor and secure your home IoT appliances
En Guarde!
Many IoT devices are so poorly protected against attacks that it is easy for an intruder to slip inside. With the right tools and best practices, you can bar the door.
The "S" in IoT stands for security – as a common saying goes. The recent history of IoT development is paved with absurd examples of security falling by the wayside. One oft-reported tale tells of a Bluetooth-controllable water closet with the pairing code 0000 that could not be changed. Another example is the smart breast pump that unexpectedly turned innocent mothers into botnet operators. But all the horror stories have not diminished the success of IoT. The army of smart helpers in households is growing all the time. Smart lights, smart thermostats, smart ovens, smart sockets, smart coffee machines …
As always: New technology brings the potential for misuse. In the context of IoT, many users do not understand the threat scenario posed by potentially problematic devices. For instance, what would an attacker gain from taking control of a smart washing machine? But things are different if you look at smart blinds and, above all, smart lighting control. Anyone who gains access to your Philips Hue configuration (Figure 1) can see when you are at home and, more ominously, when you are not. This information is a wonderful tool for planning break-ins. Insecure thermostats on radiators can also become a problem; imagine if a mischievous teenager or angry neighbor could turn your apartment into a sauna. If they do this in a clever way and then change the access credentials for the thermostat control center, your heating will keep running at full blast without you being able to do anything about it.

As is so often the case in the IT context, it is better to be safe than sorry when it comes to IoT. Anyone operating IoT devices at home will want to consider a few factors to boost security. What should you look out for when purchasing IoT devices? What software is available to fend off attacks? What tools will help you be aware that something is going wrong?
The Right Hardware
Security starts with choosing the right hardware. One factor divides IoT devices into two groups: WiFi connectivity. A device that operates on an ordinary WiFi network might seem convenient, but keep in mind that this device is then vulnerable to all the attacks intruders use for compromising WiFi networks. On the other hand, some IoT devices use protocols and standards that are adapted to a specific purpose with security in mind: First and foremost of these is the Zigbee protocol suite. A Zigbee network is also a wireless LAN, but it transmits on its own frequencies and cannot be used as a normal WiFi at all, and that is something that contributes towards security. A network that offers no vectors for extensive attack scenarios is less vulnerable from the outset.
The ranks of Zigbee devices today include solutions for smart room lighting, including Philips Hue. Many thermostats for radiators also rely on communication based on the Zigbee standard. However, a communication gateway is needed to mediate between the Zigbee devices and the administrator. In most setups, this gateway is the hub, as found in the Philips Hue example. It has one leg in the Zigbee world, and the other is a node on the normal network and therefore a good starting point for your defense against attackers.
The first line of defense in the fight against IoT attacks is always the hardware manufacturer. The manufacturer has a duty to provide its own users with regular updates to remedy known bugs. All told, the premium manufacturers have a good performance record for maintaining their devices with updates. But if you order your smart lamps from an unknown company, you could be bringing problems into your home. If a vulnerable device is connected to the network but is no longer updated by the manufacturer, it becomes a dangerous point of attack for an intrusion.
As an administrator of a local network, however, you are not completely unprotected. The vast majority of routers and WiFi access points offer the ability to run multiple networks locally. You then have the option of configuring a guest network with specific parameters you can define in detail. You can therefore use a guest network to boost IoT security by isolating the IoT devices on a separate network segment.
You can define a general block for incoming and outgoing packets for an IoT network on most routers. The idea is that the devices on the network do not need to generate traffic for the outside world or receive traffic that the administrator has not explicitly allowed through the firewall beforehand. The main reason why this protection is so difficult is that not every manufacturer tells you the systems on the network with which its devices want to communicate. Trial and error, supplemented by a Google search, are usually the means for finding the answer.
Segmentation keeps the extent of damage from an attack as small as possible. Even an attacker who succeeds in compromising the IoT network does not automatically have access to the rest of the assets.
If there are devices on the home network that are directly connected to the network via WiFi and that do not rely on Zigbee, well-segmented WiFi networks are almost essential for survival. It is almost obligatory to shield devices of this type from the rest of the environment.
Focus on the Router
In many places today, the router is a network component whose existence users are no longer even aware of. The concept of masquerading and NAT is so ubiquitous today that it seems quite normal to have such a device somewhere. But this can also work the other way around, like the case involving the people from Magenta-T, who delivered their Speedport routers with security "features" implemented so incorrectly that normal email was no longer possible, prompting frustrated users to immediately disable all the security features on their devices.
In the context of IoT security, the router plays an important role for several reasons. Consider the case of Universal Plug and Play (UPnP), a protocol designed for multimedia devices such as audio players or cameras to make it easier for devices to find each other. In principle, it is fine to use UPnP within your own four walls. But some routers and ISPs configure devices to forward UPnP announcements from the LAN to the outside world. For example, if you want to monitor what your dog is doing in your apartment while you're away, and you buy a cheap IP camera from a discount store, you could theoretically stream live video from your own home to the web – 24 hours a day. If you think this is an exaggerated scenario, please refer to Shodan (Figure 2). The service collects announcements from all over the world and catalogs them so that you can immediately connect to the cameras streamed to the network.
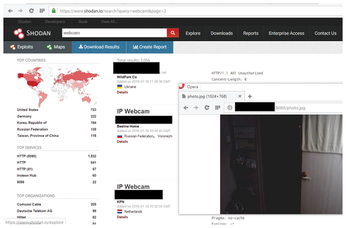
If you want to prevent remote attackers from getting control of your devices, the number one rule is to change the default password on every IoT device, without exception, as soon as it goes live in your home. In addition, you need to take the time to check your own router's security settings more carefully if you have not done so thus far. Whatever else you do, you have to avoid streaming UPnP announcements to the Internet, because this function opens the door to misuse.
Searching for Vulnerabilities
Isolation and best practices can help minimize the potential attack vector in the IoT context, but if you make massive use of IoT devices, these precautions might not be enough. You'll also need to actively secure your own network by using software that detects existing vulnerabilities and alerts you to them.
It's obvious that if you use dozens of IoT devices from several different manufacturers, it's almost impossible to keep track of all their security announcements. Instead, a tool that actively points out an exploitable vulnerability as it occurs relieves the burden on the operator and implicitly makes monitoring more efficient. A vulnerability scanner of this type is available for Linux. The OpenVAS scanner comes from Greenbone and is part of the Greenbone Community Edition. OpenVAS stands for Open Vulnerability Assessment Scanner.
OpenVAS evaluates periodic security advisories from bodies such as CERT or CVE, defines machine-readable criteria by which it identifies a system as vulnerable, and enables batch-mode searches. Under the hood, OpenVAS is a bit like a classic antivirus program. It tries to find affected systems based on signatures. The OpenVAS scanner finds not only specific malware but also specific firmware versions on target devices.
Keep in mind that most IoT devices contain a small computer that exposes details such as the kernel or SSH version to the outside world. If OpenVAS is unleashed on a local network, it first identifies the active systems and then checks them for potential problems using its database. This check can take place without any manual intervention.
If you want to run your own OpenVAS instance on the local network, it makes sense to use separate hardware to do so. A recent Raspberry Pi has enough RAM and CPU capacity to run OpenVAS. You will need a largish SD card in the device to store the necessary files.
The manufacturer offers the components required for OpenVAS in the form of handy Docker containers, also for the Raspberry Pi. The documentation explains how to quickly get the community edition of OpenVAS running in a container on a Raspberry Pi. This approach is highly recommended: You only need a Raspberry Pi and the appropriate Docker compose file for this kind of deployment [1].
OpenVAS includes several components in the background, and they only deliver meaningful results when working together. Using the Docker Compose option, you can roll them out simultaneously and in a perfectly coordinated way. The alternative is a manual rollout also described in the documentation.
Once you have started all services on the Raspberry Pi via Docker Compose, the next step is to check out the dashboard (Figure 3). Connect to the Raspberry Pi via SSH, and then run the command from Listing 1 – at least if your PC is running a graphical interface. X11 is available for both macOS and Windows; if you want to access OpenVAS from a Linux desktop, you need to enable X protocol forwarding in SSH, then you will be up and running.
Listing 1
Calling OpenVAS
The Greenbone Security Assistant is a web application that opens in your browser when you connect to the OpenVAS scanner. At the top of the screen are various buttons for central tasks. The most important of these will be Scans. You only need to define the network you want OpenVAS to investigate, and off you go. The scanner reliably finds devices based on Linux or similar operating systems with signatures that map to a specific vulnerability in the CERT or CVE vulnerability database (Figure 4).
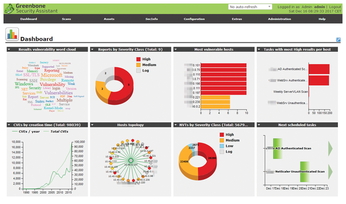
You can use the admin interface to enable notifications. If configured to do so, Greenbone Security Assistant can periodically scan the local network and email the results to the admin.
By the way, it's not just the IoT device zoo on a network that benefits from running OpenVAS. The scanner also finds unresolved vulnerabilities in normal systems, such as desktop computers or laptops running macOS, Windows, or Linux.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
So Long Neofetch and Thanks for the Info
Today is a day that every Linux user who enjoys bragging about their system(s) will mourn, as Neofetch has come to an end.
-
Ubuntu 24.04 Comes with a “Flaw"
If you're thinking you might want to upgrade from your current Ubuntu release to the latest, there's something you might want to consider before doing so.
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.
-
Linux Usage Increases in Two Key Areas
If market share is your thing, you'll be happy to know that Linux is on the rise in two areas that, if they keep climbing, could have serious meaning for Linux's future.
-
Vulnerability Discovered in xz Libraries
An urgent alert for Fedora 40 has been posted and users should pay attention.

