Anonymity with ProxyChains
Leaking Everywhere
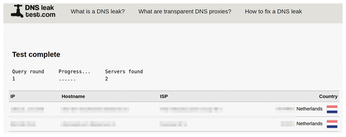
To make sure that I am not leaking any DNS lookups to third parties, I'll use a clever site called DNSleaktest.com [15].
Visit the site in Firefox (with proxying enabled), and then run the Standard test (Figure 9). If you are connected to a VPN and some servers displayed aren't associated with that VPN service, then you have a DNS leak.
Conclusion
ProxyChains is an anonymity tool that can operate with or without the Tor network. If you get stuck, a top troubleshooting tip is to make sure your laptop's system clock is precisely set. The simplest way to set the system clock is to just install the ntpdate package and manually run the update command. The following example shows a global NTP server pool, but you can adjust the command to your region if needed:
$ apt install -y ntpdate $ ntpdate -v pool.ntp.org
I hope that you have been suitably impressed with the undeniably sophisticated ProxyChains and the remarkable Tor network. Setting up ProxyChains is simple and painless, with a useful outcome that other software struggles to get close to.
There are many applications that you can push through a proxy chain using TCP-based traffic or via the Tor network. I'd suggest practicing with a variety of packages.
As a reminder, you should use your newly found knowledge ethically and wisely.
Infos
- ProxyChains: https://github.com/haad/proxychains
- TryHackMe: https://tryhackme.com
- "How Does ProxyChains Avoid DNS Leaks?": https://security.stackexchange.com/questions/224394/how-does-proxychains-avoid-dns-leaks
- ProxyScrape: https://www.proxyscrape.com/free-proxy-list
- PROXY-List on GitHub: https://github.com/TheSpeedX/PROXY-List
- Free Proxy List: https://free-proxy-list.net
- "What is SOCKS5 and Why Should I Use It": https://securityintelligence.com/posts/socks-proxy-primer-what-is-socks5-and-why-should-you-use-it
- Scanme at nmap.org: http://scanme.nmap.org
- The Tor Project: https://www.torproject.org
- FoxyProxy: https://addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard
- Burp Suite: https://portswigger.net/burp
- What's My IP: https://whatsmyip.com
- Nmap network scanner: https://nmap.org
- Nmap scanning options: https://nmap.org/book/port-scanning-options.html
- DNS Leak Test: https://www.dnsleaktest.com
« Previous 1 2
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
OSJH and LPI Release 2024 Open Source Pros Job Survey Results
See what open source professionals look for in a new role.
-
Proton 9.0-1 Released to Improve Gaming with Steam
The latest release of Proton 9 adds several improvements and fixes an issue that has been problematic for Linux users.
-
So Long Neofetch and Thanks for the Info
Today is a day that every Linux user who enjoys bragging about their system(s) will mourn, as Neofetch has come to an end.
-
Ubuntu 24.04 Comes with a “Flaw"
If you're thinking you might want to upgrade from your current Ubuntu release to the latest, there's something you might want to consider before doing so.
-
Canonical Releases Ubuntu 24.04
After a brief pause because of the XZ vulnerability, Ubuntu 24.04 is now available for install.
-
Linux Servers Targeted by Akira Ransomware
A group of bad actors who have already extorted $42 million have their sights set on the Linux platform.
-
TUXEDO Computers Unveils Linux Laptop Featuring AMD Ryzen CPU
This latest release is the first laptop to include the new CPU from Ryzen and Linux preinstalled.
-
XZ Gets the All-Clear
The back door xz vulnerability has been officially reverted for Fedora 40 and versions 38 and 39 were never affected.
-
Canonical Collaborates with Qualcomm on New Venture
This new joint effort is geared toward bringing Ubuntu and Ubuntu Core to Qualcomm-powered devices.
-
Kodi 21.0 Open-Source Entertainment Hub Released
After a year of development, the award-winning Kodi cross-platform, media center software is now available with many new additions and improvements.

