Encryption with VeraCrypt
Keeping Secrets

© Lead Image © Stefan Redel, fotolia.com
Protect your data and operating system from prying eyes with VeraCrypt.
Confidentiality and integrity are increasingly important when it comes to security. The ability to encrypt data carriers is decisive in this battle, especially for mobile devices. This article shows you how to reliably protect your data and operating system with the open source VeraCrypt tool, as well as how to completely hide the encrypted containers if necessary.
In response to the increase in awareness of IT security, Microsoft began developing the software later known as BitLocker [1] for encrypting files, partitions, or entire hard disks in 2004. BitLocker came under suspicion during the Snowden incident, when it was suspected of possibly providing backdoors or master keys for intelligence services. However, this has never been confirmed and is unlikely to be confirmed any time soon. BitLocker is therefore often used in corporate settings because it gives administrators the ability to create backup keys and store them in Active Directory, for example.
Created at virtually the same time, the free TrueCrypt [2] encryption tool was based on Encryption for the Masses (E4M) source code (which was allegedly stolen from SecurStar) [3]. While it took BitLocker another three years to find its way into Windows, TrueCrypt enjoyed great popularity right from the start, although the developers remained anonymous for a long time and its source code was not freely available. Rumors later confirmed that TrueCrypt's development originally came from criminal circles. TrueCrypt announced the end of development in 2014.
In 2013, VeraCrypt, a fork based on an older, audited version of TrueCrypt, was launched. Today, VeraCrypt is developed by the open source community. Of particular interest, VeraCrypt supports the different Linux derivatives and macOS as operating systems in addition to Windows. As an added bonus, legacy TrueCrypt containers can easily be recycled thanks to VeraCrypt.
Encryption for Data Protection
Data confidentiality and system integrity are fundamental protection goals of IT security and must therefore be taken into account whenever an operating system is installed. Regardless of the industry, virtually everywhere you look there is sensitive data that needs protecting (often for legal reasons). Whether construction plans, customer data, customer projects, or simply internal documents and communication, you don't want this information falling into the wrong hands.
Mobile devices and data carriers in particular are exposed to a greater risk of loss or theft, especially if you have to hand the device over briefly, say, during international travel. In these cases, an encrypted system partition protects against uncontrolled manipulation, such as the installation of malware or spyware. Above all, however, it protects against unauthorized access, for example, to industrial secrets or personal data on the hard drive.
Of course, confidentiality and integrity are only ensured when the computer is switched off. If a device is switched on and the encrypted data is unlocked for daily work with a password, access is possible. A loss of confidentiality due to user error or manipulation by malware is then possible.
Setup and First Steps
Some corporate environments already use VeraCrypt. There are different configurations, depending on the intended use. Various scenarios are outlined below. To get started, you first need to download VeraCrypt for installation on your operating system. Use the official download page [4] provided by the IDRIX developers. This way you can count on having a valid, signed version and avoid the trickery of dubious download platforms.
The installation is child's play: Launch the downloaded file with admin authorization or confirm the prompt during the install. Then select the language that suits you and install VeraCrypt with the standard options. Alternatively, you can download the source code provided on GitHub [5] and create VeraCrypt on your own system.
When you launch VeraCrypt, the program comes up with a tidy interface (Figure 1). You will see an overview of the mounted drives; VeraCrypt uses the classic drive letters from A to Z on Windows and also offers the option of mounting or creating a container or an encrypted partition.
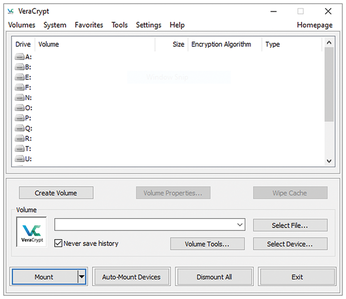
Pressing the Create Volume button opens a dialog that guides you through the process. The first step is to select the type of storage you want for the volume. You can choose between a container file, an encrypted partition on your hard disk, or an encrypted system partition of your Windows operating system. For first time users, it makes sense to create an encrypted container.
Next you need to define your container's volume type. You have two volume options: standard and hidden (Figure 2). Hidden volumes support two protection objectives: plausible deniability and confidentiality. A hidden volume makes it possible to deny the very existence of the encrypted data if someone tries to force you to hand over the data. To do this, you need to create a hidden volume on a standard volume. VeraCrypt creates the matching structures in the container headers regardless of which volume type you choose, so the existence of these structures alone is not credible proof of the existence of a hidden volume. Technically, the internal volume is simply a storage area within a standard volume and is protected with another secret.
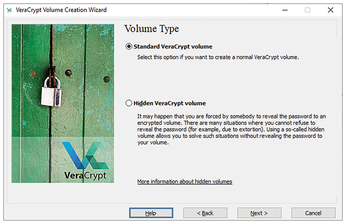
If you enter both secrets when mounting the volumes, VeraCrypt determines the byte limits of the two volumes within the container and you can safely access both volumes as required. If you only specify the secret for decrypting the outer volume, there is a risk of overwriting the hidden volume. VeraCrypt then knows nothing about the corresponding byte limits and simply fills up the container, possibly also using up the area containing the hidden volume.
Security vs. Performance
For my example, I'll select Standard VeraCrypt volume and then press Next. Then I need to select the container file's storage location and specify the encryption parameters. VeraCrypt offers a choice of algorithms. AES is the globally recognized standard for block encryption. The alternatives, Serpent and Twofish, were also candidates for the AES standard at the time, so they are comparatively secure.
If you do not trust any algorithm on its own, you can also select a cascade of several methods. You have to decide for yourself whether this makes sense cryptographically and for your application. Ultimately, cascading increases key material and eliminates the mathematical uncertainties of individual procedures in an attack scenario. The same applies to the choice of the hash method; again different variants are available. Under normal circumstances, AES and SHA-512 are safe choices that achieve a good compromise between security and performance. I will use these two methods in my example.
As the next step, you need to define the size of the volume based on your estimated needs. Otherwise, you might use up a large amount of storage space on your data carrier just to encrypt a few files or a bunch of small files. VeraCrypt also offers dynamic containers if you can't estimate the exact requirements right now. These containers do not grab the entire storage space when they are created, but simply grow to the specified maximum size as required. Incidentally, you need to choose dynamic containers carefully, because if they end up exceeding the actual hard disk capacity, there is a risk of data loss. I will be using a container size of 1GB.
You now need to select the secret for accessing the volume you created by filling out the two input fields with your choice of password. Be sure to read the info at the bottom of the dialog to help you choose a secure password. Good passwords should not only consist of many different characters, but should also be as long as possible. Password length has a major influence on security (see the "Password Security" box), although you are likely to find different recommendations for this in different places. VeraCrypt warns you if your password has fewer than 20 characters.
Password Security
Secure passwords are long. They are designed to provide protection against brute force attacks (i.e., attacks in which all possible character combinations are tested in an automated process). This complexity results from the number of characters that the attacker must try in all possible combinations. The more characters you combine, the exponentially more difficult the password becomes to crack.
However, a password's security is not only determined by the choice and number of characters, but also by the degree of secrecy. Sufficiently complex, yet easy to remember passwords do not need to be written down. The sheer number of password characters plays a greater role than the largest possible character set: An 18-character password in which you only use lowercase letters and numbers (i.e., 36 possible characters each) has more combinations than a 14-character password with 100 possible characters. To keep the secret, do not use your passwords for multiple purposes, but create an individual password for each account. Otherwise, the number of attempts required to access your files will be exactly one if your password falls into an attacker's hands (i.e., if another account that uses the same password is hacked).
As an alternative or in addition to the password, you can select further "secrets" to protect your volume. In addition to a smartcard, any file or the files of an entire folder can be defined as keyfiles (Figure 3). Of course, this increases the size of the input variable for encryption immensely, but limits the secret to be remembered to this one file or the selected combination of files. Because an attacker with access to your computer could try out any file as a secret, it is not a good idea to solely rely on one file as the secret.
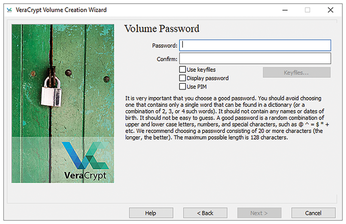
You can enhance security even further by defining the Personal Iterations Multiplier (PIM) yourself and selecting the Use PIM option. This lets you change the number of iterations of the key derivation function that generates cryptographic keys from your input, thus making brute force attacks more difficult. Having said this, the default number of iterations (500,000 rounds) offers a good compromise between performance and security, so I wouldn't change anything here.
Buy this article as PDF
(incl. VAT)
Buy Linux Magazine
Subscribe to our Linux Newsletters
Find Linux and Open Source Jobs
Subscribe to our ADMIN Newsletters
Support Our Work
Linux Magazine content is made possible with support from readers like you. Please consider contributing when you’ve found an article to be beneficial.

News
-
First Release Candidate for Linux Kernel 6.14 Now Available
Linus Torvalds has officially released the first release candidate for kernel 6.14 and it includes over 500,000 lines of modified code, making for a small release.
-
System76 Refreshes Meerkat Mini PC
If you're looking for a small form factor PC powered by Linux, System76 has exactly what you need in the Meerkat mini PC.
-
Gnome 48 Alpha Ready for Testing
The latest Gnome desktop alpha is now available with plenty of new features and improvements.
-
Wine 10 Includes Plenty to Excite Users
With its latest release, Wine has the usual crop of bug fixes and improvements, along with some exciting new features.
-
Linux Kernel 6.13 Offers Improvements for AMD/Apple Users
The latest Linux kernel is now available, and it includes plenty of improvements, especially for those who use AMD or Apple-based systems.
-
Gnome 48 Debuts New Audio Player
To date, the audio player found within the Gnome desktop has been meh at best, but with the upcoming release that all changes.
-
Plasma 6.3 Ready for Public Beta Testing
Plasma 6.3 will ship with KDE Gear 24.12.1 and KDE Frameworks 6.10, along with some new and exciting features.
-
Budgie 10.10 Scheduled for Q1 2025 with a Surprising Desktop Update
If Budgie is your desktop environment of choice, 2025 is going to be a great year for you.
-
Firefox 134 Offers Improvements for Linux Version
Fans of Linux and Firefox rejoice, as there's a new version available that includes some handy updates.
-
Serpent OS Arrives with a New Alpha Release
After months of silence, Ikey Doherty has released a new alpha for his Serpent OS.

